
Introduction
If you’re building a connected medical device or SaMD, an FDA ready penetration test is one of the clearest ways to prove your cybersecurity controls work in the real world and to reduce the risk of delays during FDA review. This guide explains what “FDA penetration testing” means, how it fits into FDA 510(k) submissions, and how to run a medical device pentest that produces reviewer friendly evidence.

What Is FDA Penetration Testing?
FDA penetration testing (often searched as medical device pentesting or FDA pentest) is a simulated real world cyberattack performed by qualified security testers to identify vulnerabilities in a medical device and its supporting ecosystem before attackers do.
Unlike a general IT pentest, medical device penetration testing typically focuses on:
- Patient safety and clinical workflow realities
- Connectivity and interoperability (device ↔ app ↔ API ↔ cloud ↔ hospital network)
- Evidence-based, repeatable testing with clear documentation
- Traceability back to your security controls and risk processes
The outcome you want is simple: credible proof that your device can withstand realistic attacks and that your security controls perform as intended.
Why FDA Penetration Testing Matters for Medical Device Compliance
Most teams searching for “FDA penetration testing” are trying to avoid one thing: getting slowed down late in the submission process because cybersecurity evidence is incomplete, unclear, or not credible.
A strong medical device pentest helps you:
- Uncover vulnerabilities scanners miss (auth flaws, chained attacks, business logic issues)
- Validate security controls (not just list problems)
- Prioritize remediation using realistic exploit paths
- Create evidence that’s useful for FDA documentation and internal quality records
- Reduce the chance of painful “we need more information” back-and-forth
This is especially important because many medical devices are highly connected and can become a path into the broader healthcare environment where they operate.

FDA 510(k) and Where Penetration Testing Fits
FDA 510(k) is a common path to market, and for connected devices and software-enabled products, cybersecurity evidence is frequently part of demonstrating the device is appropriate for its intended use and environment.
Penetration testing supports your broader cybersecurity work by providing:
- Verification that controls work as designed (auth, access control, encryption, update integrity)
- Demonstration of realistic attack resistance across key interfaces
- Documentation of scope, timeframe, methods, and results
- A point-in-time snapshot of security posture (with a plan to maintain it postmarket)
The practical expectation: saying “we did a pentest” isn’t enough. You want a report that clearly shows what was tested, how it was tested, what was found, and what changed after remediation.
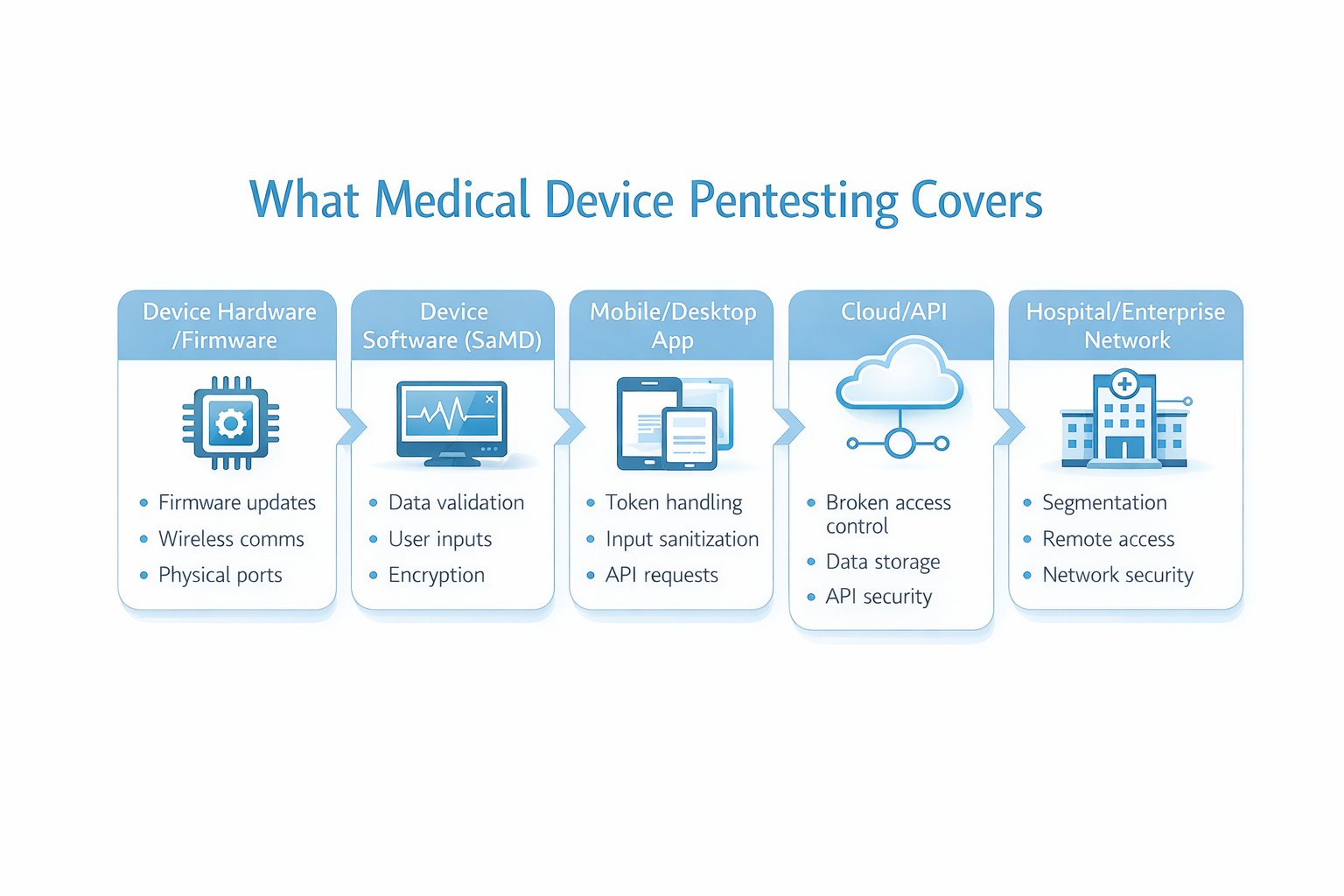
What Should Be In Scope for Medical Device Pentesting?
A common reason FDA related pentests fall short is scope mismatch. Medical devices are rarely “just the device” they’re ecosystems.
A high-quality medical device penetration test usually includes:
Device hardware and firmware
- Firmware update mechanisms (signing, integrity checks, rollback/downgrade prevention)
- Exposed services/ports and insecure defaults
- Debug interfaces and hardcoded secrets (when applicable)
- Wireless communication security (BLE/Wi-Fi/cellular where used)
Device software and SaMD
- Input handling and misuse cases
- Authorization boundaries and role enforcement
- Logging and detection behaviors (what would you see if someone tried this?)
Companion apps (mobile/desktop)
- Token/session storage and leakage paths
- Insecure local storage of sensitive data
- Abuse of app-to-API trust assumptions
Cloud, APIs, and web portals
- Broken access control (IDOR/BOLA) and privilege escalation paths
- Multi-tenant isolation failures (if applicable)
- Excessive data exposure via APIs
- Rate limiting and brute-force resistance
- Misconfigurations (public storage, overly permissive CORS)
Integrations and deployment assumptions
- Remote support channels
- Third-party components and dependencies
- Network segmentation assumptions (what happens if those assumptions fail?)
Bottom line: FDA penetration testing is strongest when it reflects how the device is actually deployed not just how it looks in a lab.
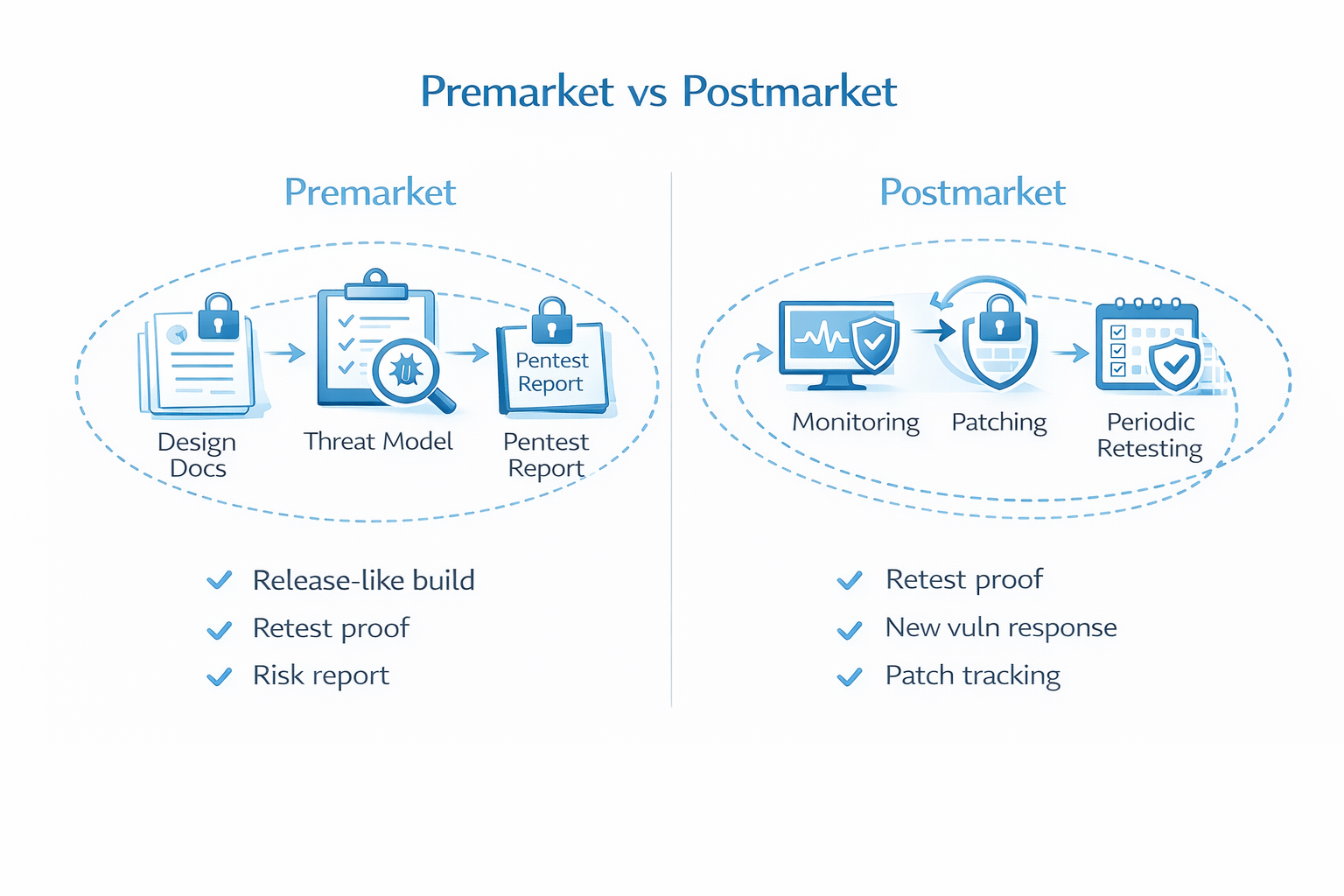
Premarket vs Postmarket: When to Run Your FDA Pentest
Penetration testing shouldn’t be a last minute checkbox. For medical devices, it’s most useful when it’s part of the lifecycle.
Premarket (before submission)
Run your pentest when:
- The system is stable enough to represent what you’ll ship
- Key interfaces are in place (device ↔ app ↔ API ↔ cloud)
- There’s still time to fix issues and retest
If the unit under test doesn’t match the final product, results may not be credible and you risk having to do it again.
Postmarket (after release)
Threats evolve, dependencies age, and environments change. A practical postmarket plan often includes:
- Retesting after major releases or architecture changes
- Periodic targeted testing of high-risk components
- Ongoing vulnerability management and monitoring activities
What an FDA-Ready Penetration Test Report Should Include
A medical device pentest report used for FDA compliance should be clear, rigorous, and defensible. Strong reports typically include:
- Executive summary (what was tested, high-level outcomes, themes)
- Scope and exclusions (explicitly what was/wasn’t tested)
- Timeframe and effort (dates, duration, team size; credibility matters)
- Methodology (repeatable steps, tools, and approach)
- Findings with evidence
- Reproduction steps
- Screenshots/logs/raw output where appropriate
- Clear explanation of impact and exploit path
- Objective technical risk factors (severity, exploitability, preconditions)
- Remediation guidance (actionable and prioritized)
- Retest results (what was verified and what remains open)
- Tester qualifications (relevant experience and who performed testing)
This style of reporting stands up better to scrutiny and helps engineering teams move quickly.

Risk Scoring: CVSS vs Patient Safety
CVSS is useful for describing technical severity, but it’s not designed to measure patient harm. A clean approach is:
- Use CVSS (or similar) for technical scoring and exploitability
- Separately describe technical effect and conditions of testing
- Keep patient safety impact discussion aligned with your internal safety risk processes (often handled separately from the pentest itself)
This avoids mixing technical vulnerability scoring with clinical safety determinations.
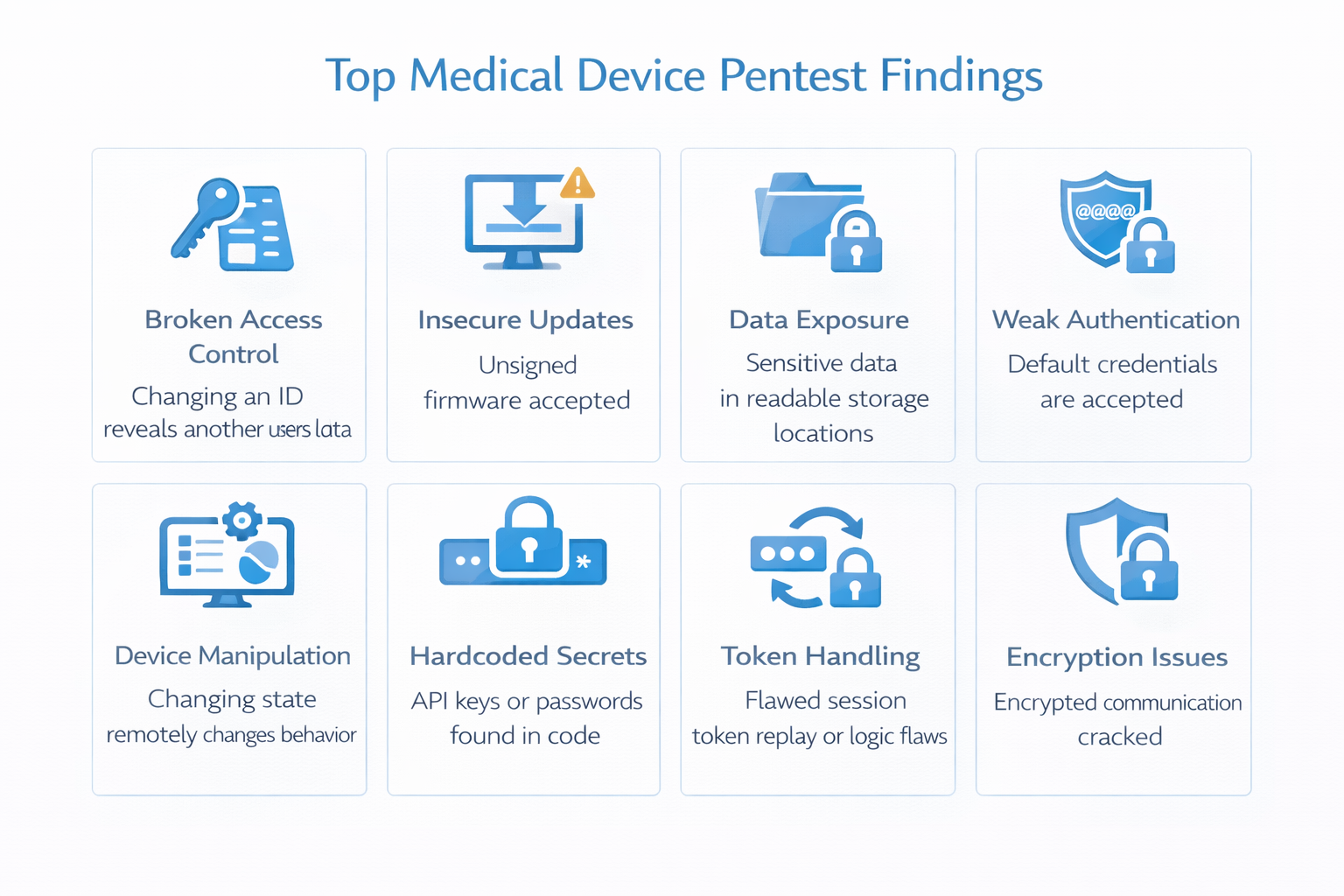
Common Findings in Medical Device Penetration Testing
Even mature teams see repeat patterns. Common issues we find during medical device pentesting include:
- Broken access control (IDOR/BOLA, missing authorization checks)
- Authentication weaknesses (token lifetime issues, insecure recovery/reset)
- Insecure APIs (object-level authorization failures, overexposed data)
- Sensitive data exposure (logs, local storage, misconfigured cloud storage)
- Insecure update mechanisms (weak integrity, downgrade paths)
- Hardcoded secrets (in firmware, apps, or deployment artifacts)
- Third-party component risk (outdated libraries/services)
- Misconfigurations (overly permissive CORS, missing headers, exposed admin paths)
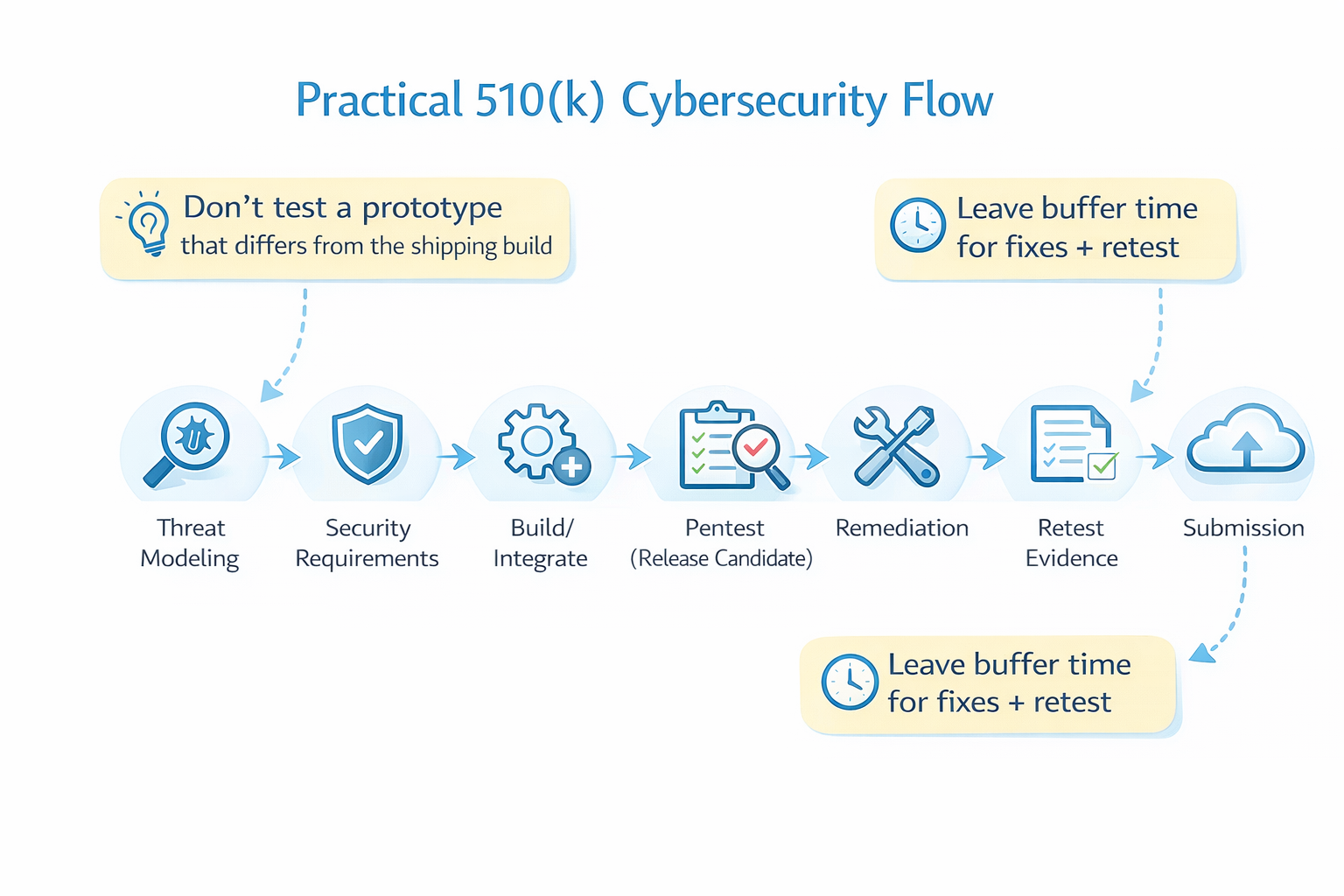
A Practical FDA Penetration Testing Checklist (510 k Friendly)
Use this to plan a pentest that supports a 510(k) timeline:
Planning
- Define system boundaries (device + apps + cloud + integrations)
- Confirm a release-like build is available for testing
- Identify key trust boundaries and data flows
- Decide the right level of access (blackbox vs graybox vs whitebox)
Scope
- Device firmware + update channel
- Companion apps
- APIs + cloud + admin portal
- Authentication + authorization (roles, tenants, object-level access)
- Logging and detection (evidence of attempted abuse)
Execution
- Validate controls, not just vulnerabilities
- Capture evidence responsibly
- Keep stakeholders aligned with regular updates
Reporting
- Clear scope + exclusions
- Dates/timeframe and effort documented
- Repeatable methodology
- Findings prioritized with actionable remediation
- Retest evidence for fixed issues
- Tester qualifications included
Why StealthNet AI for FDA Penetration Testing
At StealthNet AI, we provide FDA penetration testing for medical devices designed to produce clear, evidence driven results that support FDA 510(k) cybersecurity expectations.
What you get:
- Ecosystem-based scoping (device + app + API + cloud)
- Evidence-rich findings with clear reproduction steps
- Prioritized remediation that engineering can execute quickly
- Retesting support so you can document progress with confidence

conclusion
FDA penetration testing isn’t about checking a box it’s about producing credible, repeatable, evidence-rich validation that supports your medical device cybersecurity story and reduces surprises during FDA review.
If you’re preparing an FDA 510(k) submission and need medical device pentesting that reflects real world threats and produces reviewer friendly documentation, StealthNet AI can help you scope, test, remediate, and retest with confidence so you can move toward clearance and get your device to market faster.
.png)




