
SOC 2 Penetration Testing Requirements : Is a SOC 2 Pentest Actually Required?
If you’re preparing for a SOC 2 audit, you’ve probably heard some version of: “You need a penetration test to pass.” Then you ask your auditor, a compliance platform, or a peer company and get three different answers.
Here’s the reality: SOC 2 doesn’t explicitly mandate penetration testing, but penetration testing is one of the clearest, auditor-friendly ways to demonstrate control effectiveness especially under the Security Common Criteria around monitoring and vulnerability management.

What is SOC 2 (and why pentesting comes up so often)?
SOC 2 is an attestation report (performed by an independent CPA firm) that evaluates controls related to the Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Most organizations pursuing SOC 2 are doing it to satisfy customer/vendor security reviews especially SaaS and cloud service providers.
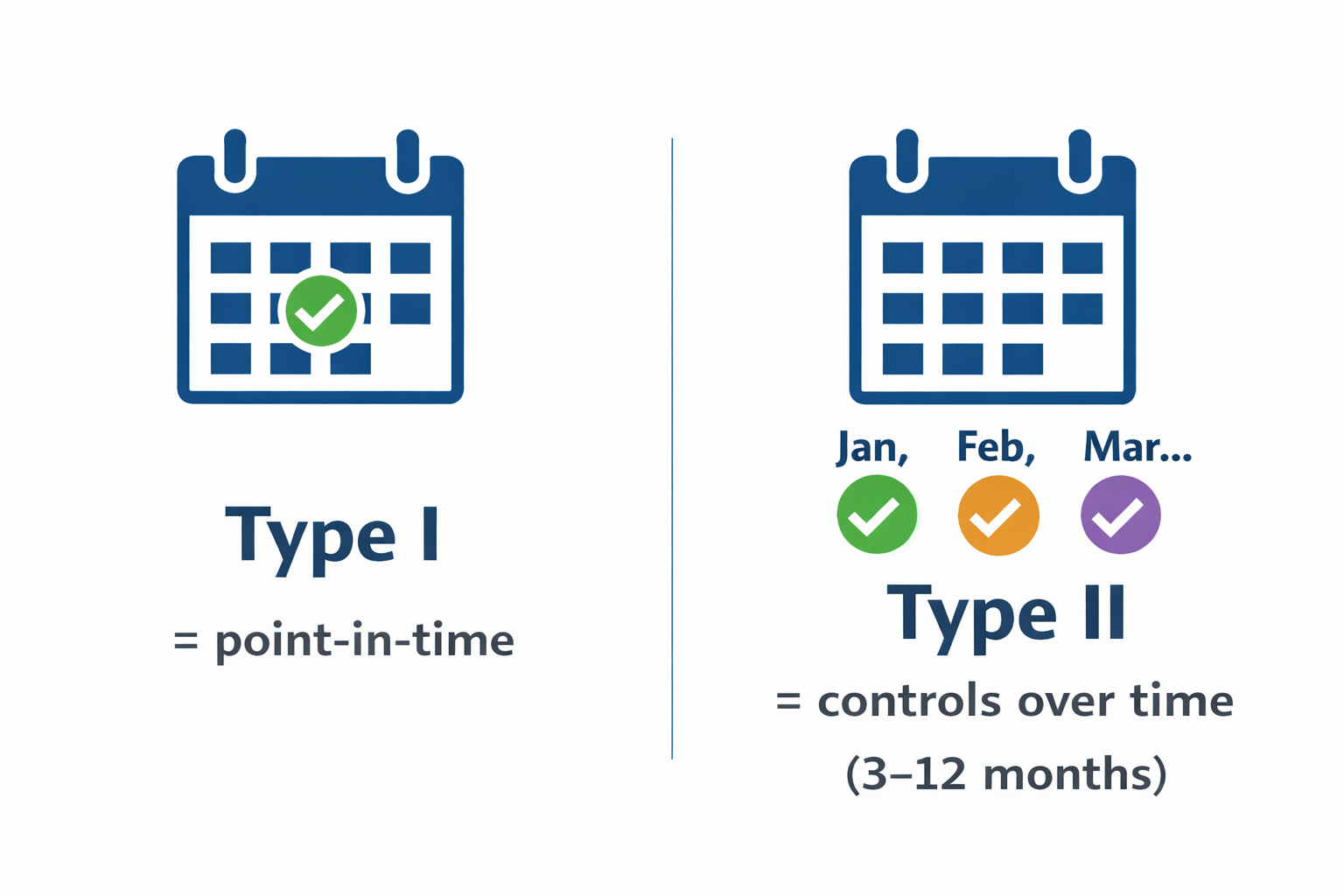
SOC 2 Type I vs Type II (quickly)
- Type I: Are controls designed appropriately and in place at a point in time?
- Type II: Do controls operate effectively over a period of time (often months)?
Where penetration testing fits into SOC 2 (the criteria that matter)
SOC 2 isn’t a checklist that says “do a pentest.” Instead, auditors look for evidence that you’re performing ongoing and/or separate evaluations of controls and that you have procedures to identify and respond to vulnerabilities.
Two commonly referenced areas:
1) CC4.1 (Monitoring Activities): “Ongoing/separate evaluations”
CC4.1 covers the idea that an organization performs evaluations to confirm controls are present and functioning. Penetration testing is a common “separate evaluation” organizations use to support this.
2) CC7.1 (System Operations): detecting vulnerabilities
CC7.1 focuses on how the organization identifies:
- changes that introduce new vulnerabilities, and
- newly discovered vulnerabilities
This is why vulnerability scanning and vulnerability management show up constantly in SOC 2 conversations even if the framework doesn’t say “must run scanner X weekly.”

Is penetration testing required for SOC 2?
Strictly speaking: no SOC 2 does not universally require a penetration test.
But here’s the practical reality:
- Many auditors and customers expect a third-party penetration test as strong evidence for monitoring/evaluation activities.
- Many SOC 2 readiness programs treat a pentest as a standard annual item (even if it’s not a literal SOC 2 rule).
What can sometimes substitute for a pentest?
Depending on your auditor and risk profile, other “separate evaluations” may help (or partially satisfy expectations), such as:
- Independent internal audit function
- Strong evidence of continuous security testing + remediation
- Certain security certifications or assessments (depending on what your auditor accepts)
The key is: your auditor has the final say on what evidence they’ll accept for your specific system and risk.
Does SOC 2 require vulnerability scanning?
Not explicitly but vulnerability scanning and vulnerability management are commonly used to support CC7.1.
In practice, many companies implement:
- recurring vulnerability scans (monthly/quarterly is common)
- patching SLAs (e.g., “critical within X days”)
- documented remediation tracking (tickets + evidence)
Penetration testing vs vulnerability scanning (what auditors actually care about)
Here’s the clean way to explain it in a SOC 2 context:
What it is :
Human-led (often manual) testing that simulates attacker behavior
Automated detection of known issues/misconfigurations
Best for:
Proving real-world exploitability, business logic flaws, chained attacks
Broad coverage, continuous detection, fast feedback
SOC 2 angle:
Strong “separate evaluation” evidence (CC4.1)
Strong vulnerability detection evidence (CC7.1)
Output:
Narrative report + evidence + remediation guidance
Findings list + severity + remediation recommendations
Many organizations do both: scanning continuously + a periodic pentest to validate controls and find what scanners miss.
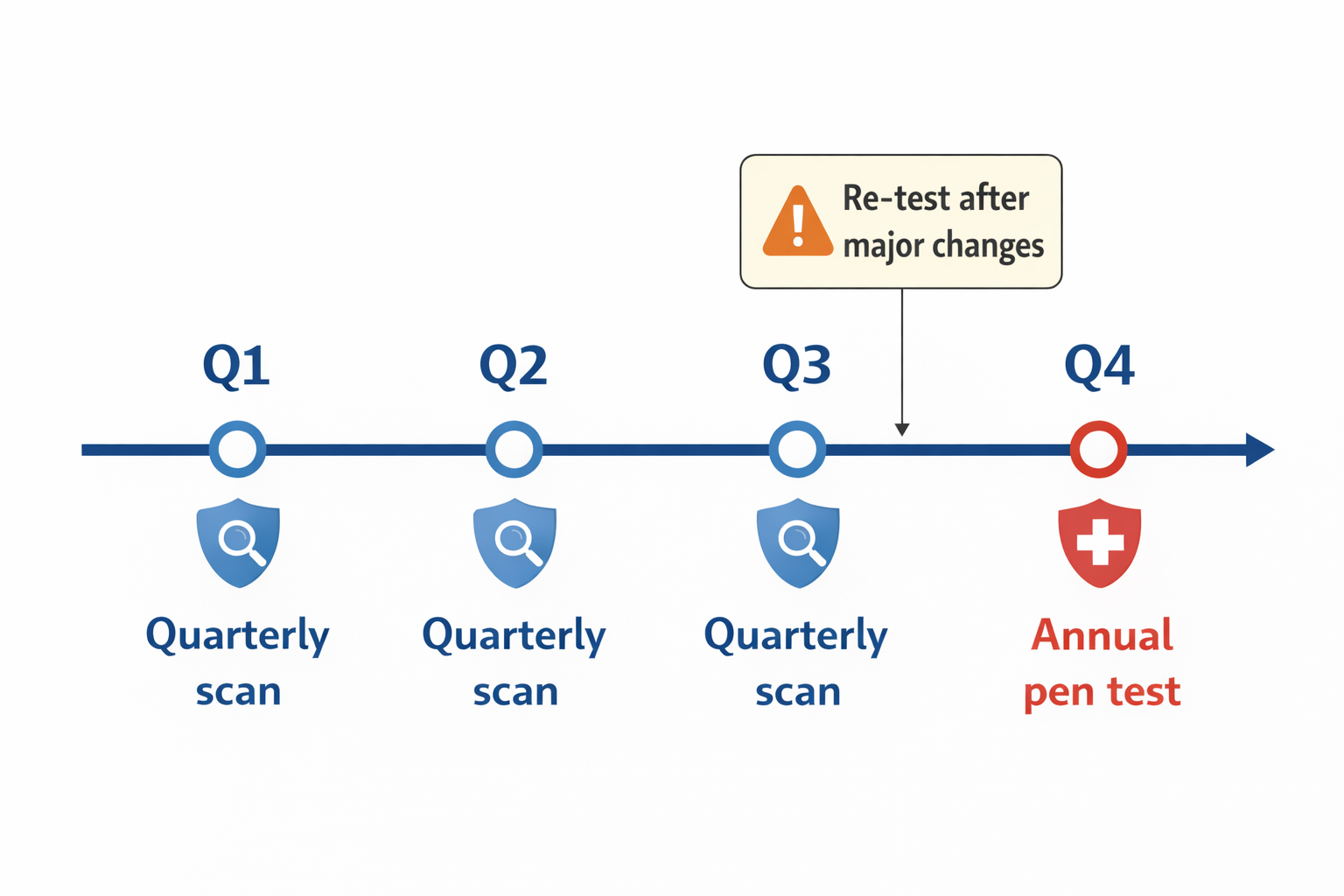
How often should you do a SOC 2 pentest?
SOC 2 doesn’t give a universal cadence, but the most common “safe” pattern organizations follow is:
- At least annually
- After significant changes (major release, infra migration, new auth model, new tenant isolation model, etc.)
What should a “SOC 2 pentest” include? (scope that won’t get rejected)
A SOC 2 pentest should generally cover what’s in-scope for your SOC 2 system description the systems that store/process/transmit customer data or support security commitments.
Common SOC 2 pentest scopes include:
- External perimeter (internet-facing IPs, VPN, gateways, WAF/CDN configs)
- Web application(s) (customer portal, admin console)
- APIs (public + partner APIs)
- Cloud configuration review (high-risk misconfigs, identity, storage exposure)
- Authentication/authorization paths (SSO, MFA, session handling, role enforcement)
If you do only one area, make sure it’s the one customers actually care about (usually web app + API, plus any critical perimeter exposure).
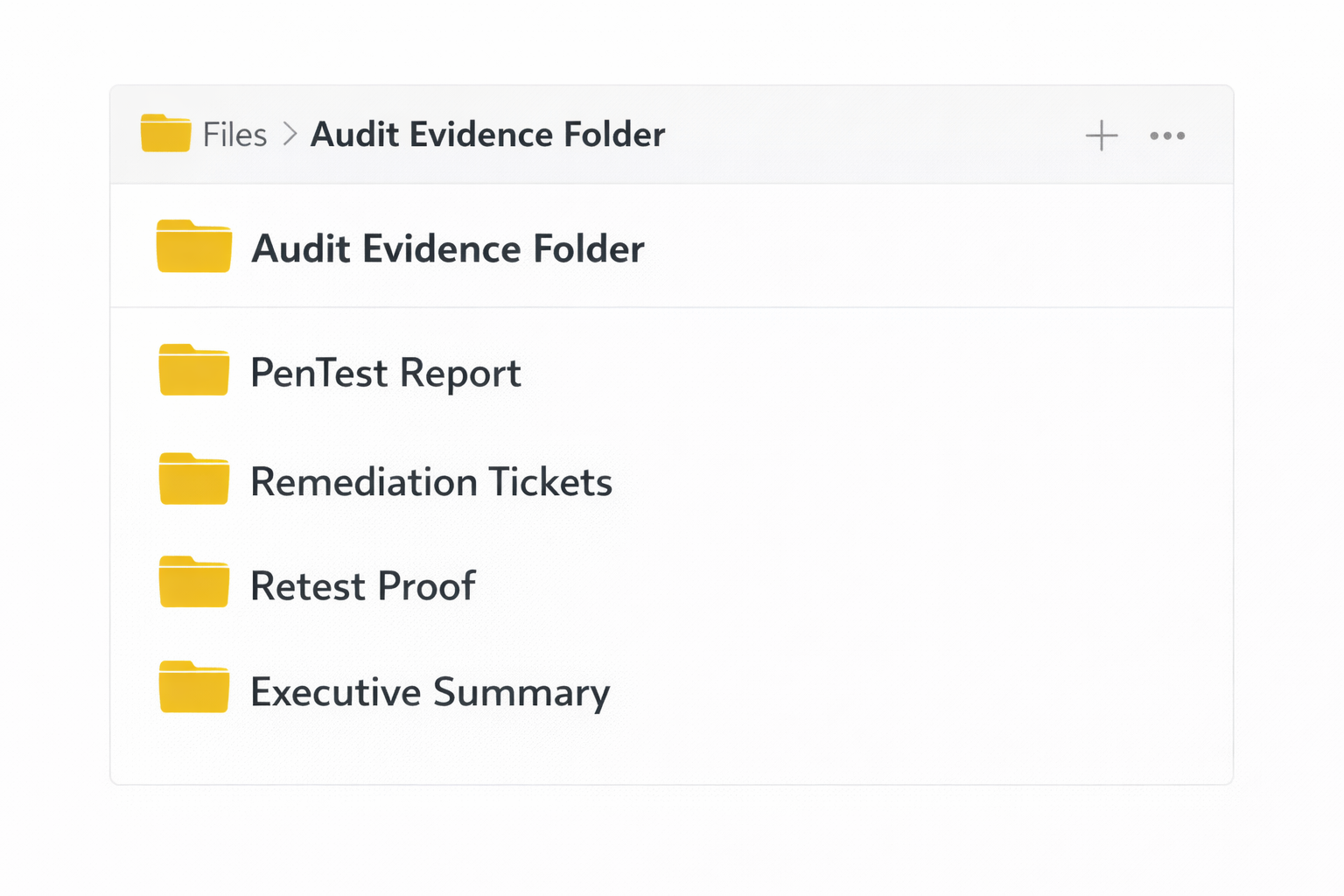
What auditors want as evidence (your SOC 2 “pentest packet”)
To make your auditor happy, aim to produce a clean evidence bundle:
- Final penetration test report (date, scope, methodology, findings, severities)
- Executive summary / attestation letter (optional but helpful)
- Remediation tracking (tickets, owners, dates, proof of fixes)
- Re-test evidence for high/critical issues (or documented risk acceptance)
This is what turns “we did a pentest” into “we have defensible evidence.”
Common SOC 2 penetration testing mistakes (and how to avoid them)
- Testing the wrong scope: pentesting a marketing site while your API handles customer data
- No remediation trail: fixing issues without tickets/evidence = auditor pain
- No retest: leaving critical items unresolved (or unverified)
- Scanner-only “pentest”: a report that’s basically automated output with little validation can create credibility issues
FAQ
Does SOC 2 require penetration testing?
No, not as a strict universal rule. But pentesting is frequently used (and often expected) as strong evidence for monitoring/evaluation activities.
Does SOC 2 require vulnerability scanning?
Not explicitly, but vulnerability detection/monitoring and vulnerability management practices are commonly used to support CC7.1.
What’s the “best” minimum approach if you want the smoothest audit?
A typical low-friction setup is:
- recurring vulnerability scanning + remediation workflow
- an annual third-party pentest scoped to your SOC 2 system
- retesting critical/high findings
Is a pentest more important for Type II than Type I?
Type II is about demonstrating controls operate effectively over time, so having repeatable vulnerability management evidence (and a well-documented pentest + remediation trail) tends to be more compelling.
Conclusion
SOC 2 doesn’t universally mandate penetration testing, but if you want to reduce audit friction and increase customer trust, a well-scoped SOC 2 penetration test paired with a real vulnerability management program is one of the most straightforward ways to demonstrate that your controls aren’t just written down, they actually work.
If you want a simple, honest takeaway you can reuse internally and externally:
SOC 2 penetration testing isn’t always “required,” but it’s commonly expected and it’s often the easiest evidence to defend.
.png)




