Introduction
If you’re searching for CMMC penetration testing, you’re probably trying to answer two questions at once: are we actually secure, and will our evidence hold up when a customer, prime, or assessor asks for proof. CMMC is moving from theory to contract reality, and more Defense Industrial Base organizations are treating a CMMC pentest as a practical requirement for protecting CUI and staying contract eligible, especially when scoping enclaves and documenting real control effectiveness.
What Is CMMC Penetration Testing
CMMC penetration testing is a structured, authorized simulation of real attacker behavior against the systems in your CMMC assessment scope, often a CUI enclave. Unlike a basic vulnerability scan, a CMMC aligned penetration test is designed to produce actionable findings plus assessor friendly evidence so you can show that security controls are operating as intended, not just checked on paper. It focuses on how an attacker would actually break in, move laterally, and access CUI.
Why Penetration Testing Matters for Defense Contractors Handling CUI
DIB organizations are targeted because they can be the entry point to sensitive programs. A well scoped pentest helps you find exploitable weaknesses scanners miss, validate segmentation between in scope and out of scope systems, confirm whether controls stop realistic tactics, and create remediation priorities that reduce breach risk and compliance risk.
Common outcomes that matter to contractors include:
- Fewer surprises during a C3PAO assessment or customer security review
- Stronger confidence that CUI protections work in real conditions
- Clear evidence you can use internally to drive fixes and funding
- A repeatable process you can run after major changes
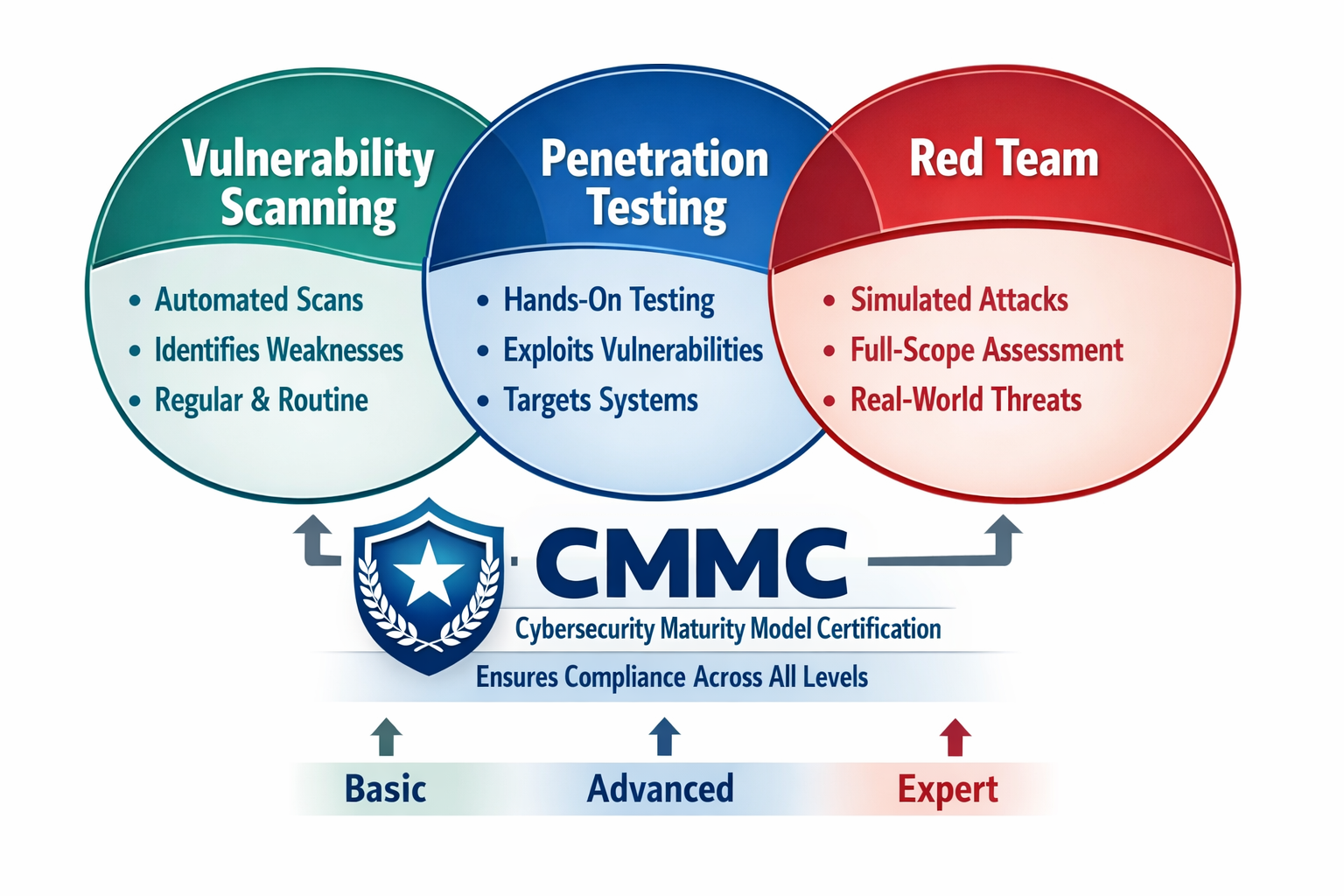
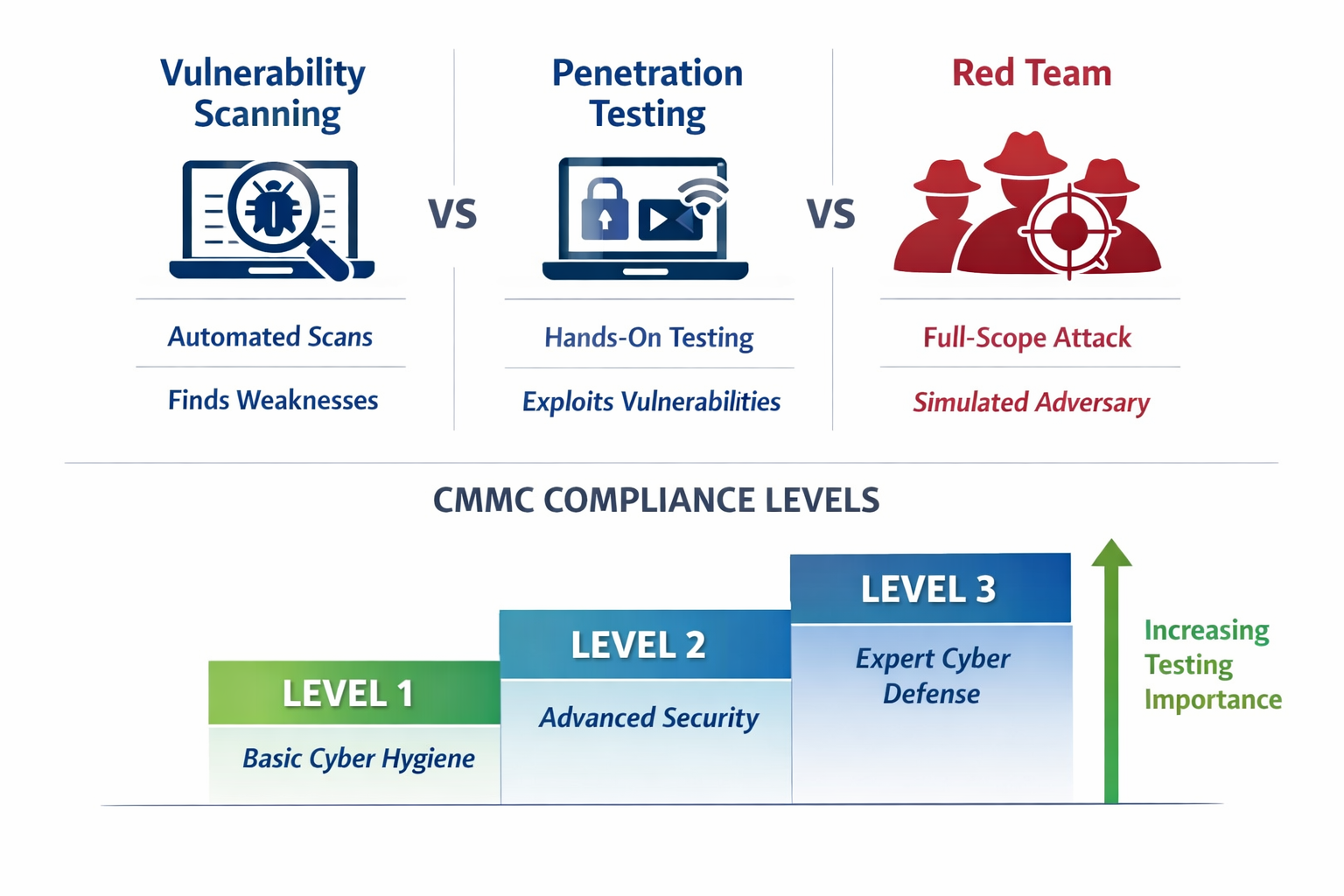
CMMC Levels 1 to 3 and Where Pentesting Fits
CMMC uses three levels tied to data sensitivity and risk. The most common CMMC pentesting conversations happen at Levels 2 and 3 because they involve CUI and deeper verification.
- Level 1: foundational controls for Federal Contract Information, pentesting is optional but still useful for internet facing exposure
- Level 2: aligned to NIST SP 800 171 for Controlled Unclassified Information, many organizations use pentesting to validate control effectiveness before assessment
- Level 3: higher risk programs with advanced requirements, penetration testing becomes a stronger expectation as maturity increases
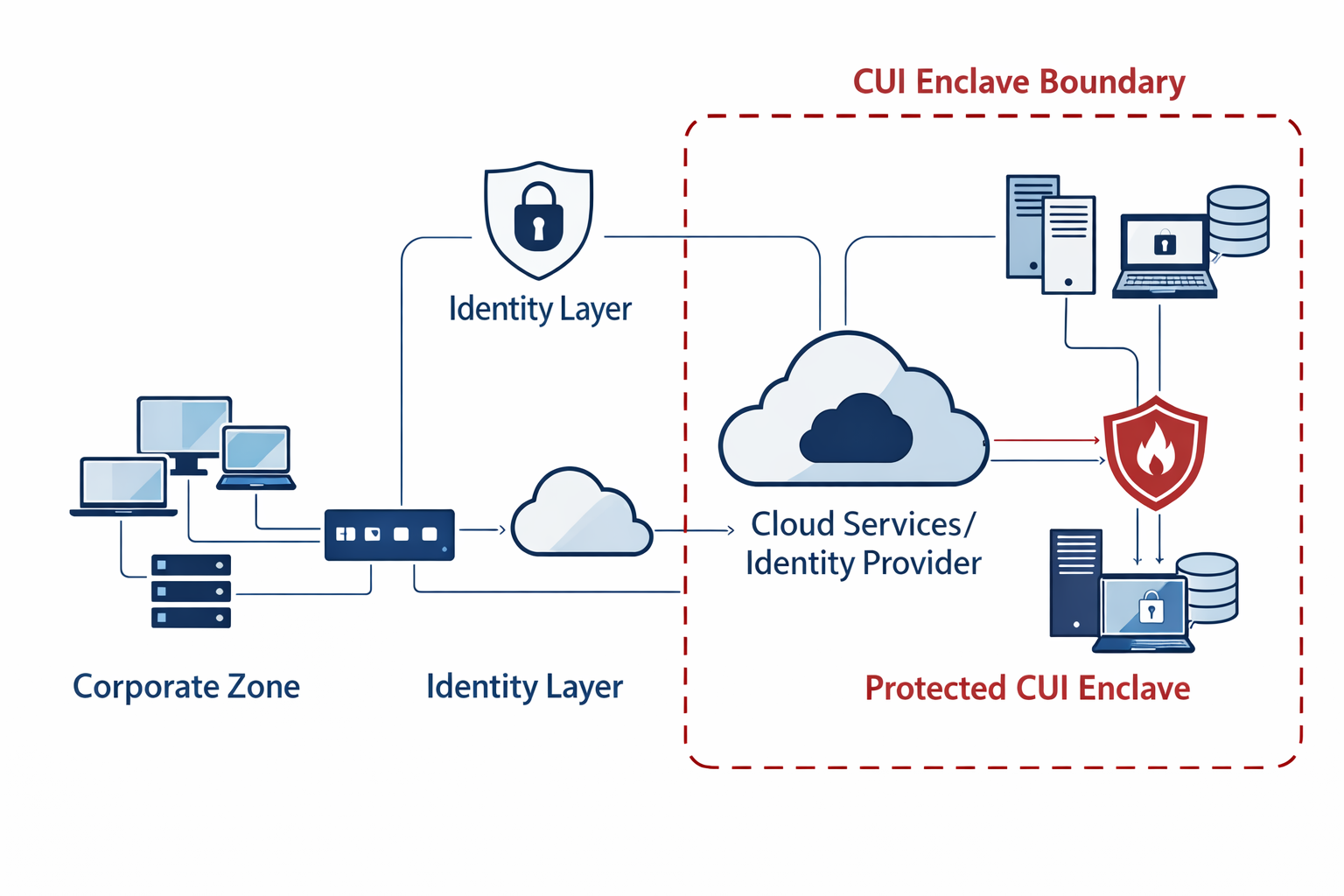
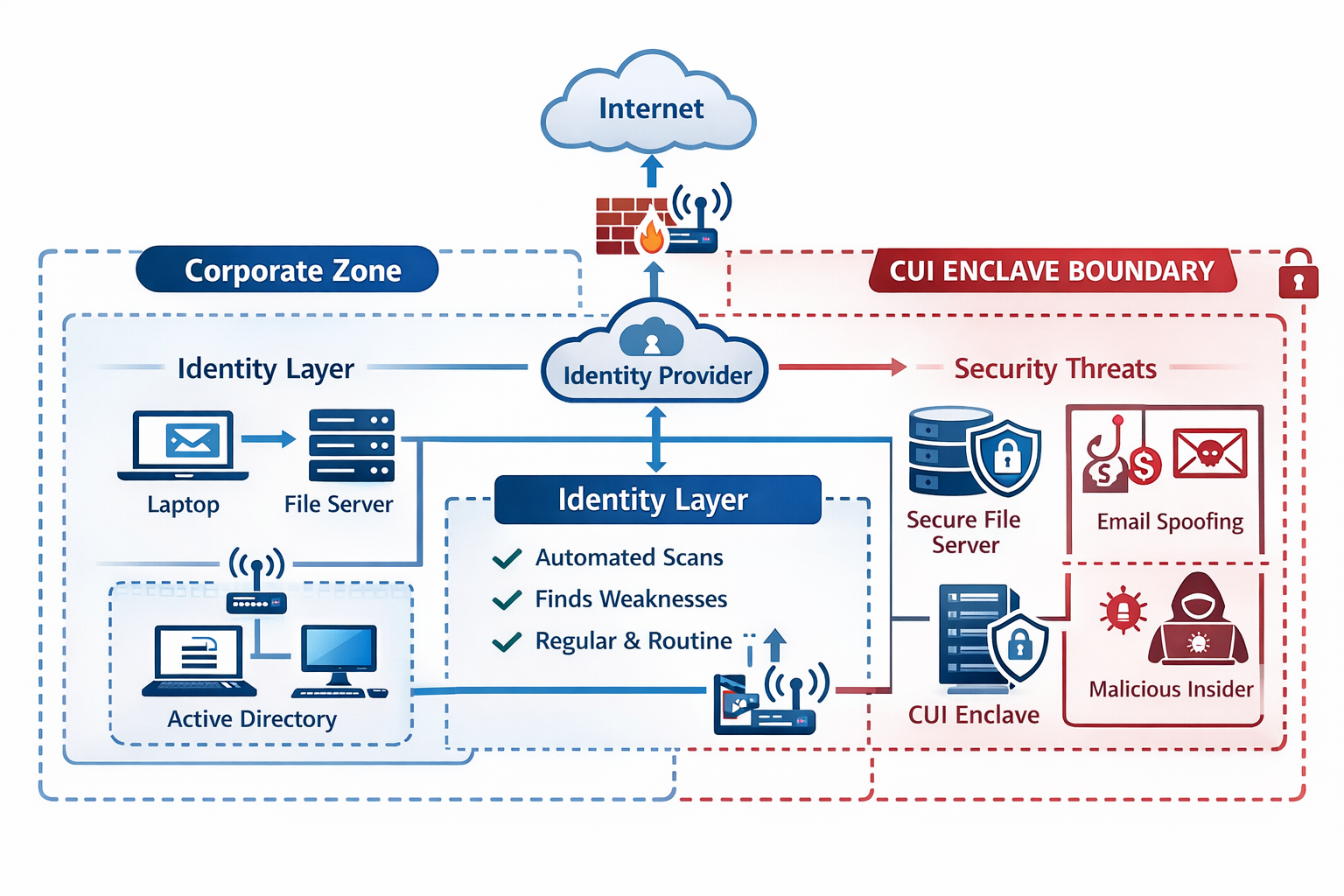
Scoping a CMMC Pentest the Right Way
The fastest way to waste money on a CMMC pentest is to scope it like a generic test everything engagement. The fastest way to miss what matters is to scope too narrowly and ignore realistic attack paths into the enclave. A CMMC ready scope starts with your assessment boundary and the systems that process, store, or transmit CUI, then expands to the pathways that could realistically lead into that boundary.
A practical scoping checklist:
- Define the CUI enclave boundary and document what is in scope
- Identify all internet facing entry points that could reach the enclave
- Include identity paths such as SSO, MFA enforcement, conditional access, and privileged roles
- Validate segmentation between corporate IT and CUI systems
- Include third party and vendor integrations that touch the enclave
- Confirm rules of engagement, safety constraints, and test windows
What a CMMC Penetration Test Should Cover
A strong CMMC pentest is not one size fits all, but most DIB environments need coverage across predictable surfaces.
Most common scope areas:
- External network testing for perimeter exposure and initial access
- Internal or assumed breach testing for lateral movement and privilege escalation
- Web application and API testing for auth, access control, data exposure, and business logic
- Identity and SSO testing for misconfigurations and excessive privilege
- Cloud and SaaS security testing for permissions, storage exposure, and logging gaps
- Segmentation testing to confirm out of scope systems cannot pivot into CUI systems

The 5 Stages of a CMMC Pentest Engagement
A CMMC pentest is a methodical process. Knowing the stages helps you prepare and keeps the work safe and productive.
- Planning and scoping: define goals, in scope assets, and rules
- Reconnaissance: map attack surface and likely entry points
- Exploitation: validate what is actually exploitable and show real impact
- Post exploitation: determine realistic blast radius and access paths to CUI
- Reporting: deliver clear findings, proof, and step by step remediation
Deliverables That Actually Help in a CMMC Assessment
A pentest that finds issues but does not produce clean evidence is a missed opportunity. A CMMC aligned pentest should produce deliverables that are usable for both technical remediation and assessment readiness.
Deliverables you should expect:
- Executive summary for leadership
- Technical findings with severity, impact, and reproduction steps
- Evidence such as screenshots, logs, and configuration proof
- Remediation guidance with validation steps
- Optional retest and a remediation validation summary
How Often Should You Run a CMMC Pentest
There is no single cadence that fits every contractor, but a practical approach is to align testing with change and risk.
A common cadence:
- Annually: full scope pentest of the CUI enclave and its access paths
- After major change: cloud migrations, identity changes, new apps, network redesigns
- Quarterly targeted tests: high change surfaces like web apps, APIs, and identity policies
If your environment changes often, a more continuous approach can reduce surprises and keep you closer to audit ready at all times.
Common Mistakes That Cause CMMC Pentests to Miss the Point
These issues show up frequently in CMMC readiness work and are worth avoiding.
- Testing assets that are not in the assessment scope
- Scoping the enclave but not testing realistic access paths into it
- Deliverables that lack evidence or are too vague to act on
- Treating vulnerability scanning as a substitute for penetration testing
- No retest plan, so fixes are not verified
- Not tying findings to systems, roles, and boundaries
Choosing a CMMC Penetration Testing Vendor
A compliance driven pentest needs both real offensive skill and compliance friendly documentation. When evaluating vendors, look for teams that can scope around a CUI enclave, test identity and segmentation pathways, provide strong evidence, and support retesting.
Questions to ask:
- Can you scope to our CUI enclave and confirm boundary testing
- Do you test identity systems and privilege pathways, not just networks
- Will the report include evidence and clear remediation steps
- Do you offer retesting and a remediation validation summary
- Can you tailor the engagement to our assessment timeline
How StealthNet AI Helps With CMMC Penetration Testing
StealthNet AI is built for organizations that need speed, clarity, and real security outcomes while preparing for CMMC. We offer three options so you can match the engagement to your maturity, timeline, and budget.
- AI automated penetration testing: fast, repeatable coverage that helps you keep up with change and quickly validate your external exposure and key pathways
- Hybrid AI plus human penetration testing: broad automated coverage plus expert testers who validate exploitability, chain weaknesses, and produce high confidence findings with strong evidence
- Manual human only penetration testing: deep human led testing for complex environments and higher assurance needs
If you are preparing for Level 2 or Level 3 readiness, a common approach is to start with hybrid to get both breadth and depth, then use automated testing to stay continuously validated between major assessments.

CMMC Penetration Testing FAQs
Is a pentest required for CMMC Level 2 ?
Many organizations treat it as a practical requirement because it validates that controls work in real world conditions and reduces surprises before assessment.
Is penetration testing expected more at Level 3 ?
Yes, expectations increase with maturity, and penetration testing fits the goal of proving defenses hold up against skilled attacker behavior.
What is the difference between vulnerability scanning and penetration testing ?
Scanning finds known issues at scale. Penetration testing validates exploitability, chains weaknesses, and shows realistic impact.
How do we keep scope from exploding ?
Start with the CUI enclave and test the pathways into it, then add only what materially affects access to CUI.
Conclusion
CMMC penetration testing helps you move from paper compliance to real confidence by proving whether your CUI protections hold up under realistic attacker behavior and by producing evidence that is useful for readiness and remediation. If you want a partner that can deliver fast results, clear reporting, and options that fit your timeline and budget, StealthNet AI offers automated, hybrid AI plus human, and manual penetration testing so you can choose the right level of depth and keep your security posture strong as requirements and threats evolve.
.png)




